Complete the programming challenge below and submit your answer below as a copy of your code or screen capture in a PDF or wordprocessed document.
Challenge Instructions
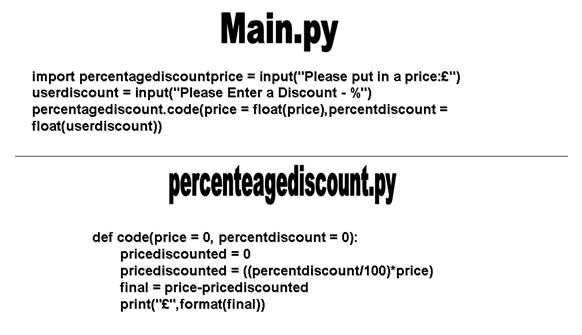
Write a program that uses an original price and a user entered discount percentage. The program should calculate the new price as a real number rounded to two decimal places.
Extension: write this as a function that takes in both the price and discount as parameters.